There’s no sense in encrypting your personal files and folders if you don’t secure them with a strong password. Today, we’re going to show you how to do just that. You’ll create an easy to remember password that will lock your material tighter than Fort Knox.
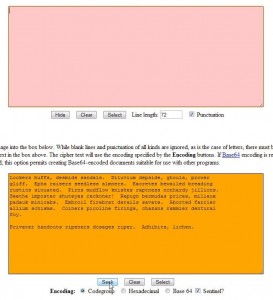
1. There are some prerequisites to this course. In order to create this special password, you have to use a number pad, either the one on the right side of your full-size keyboard or the numbers you can access using the FN key on a laptop, for instance. Yes, there are numbers across the top of every keyboard but those are not the ones we want to use here. If you always use a full-size keyboard, make sure the NumLock key is pressed down. If not, figure out how to use the ‘other’ numbers, usually on the top of certain keys, like this:

On this keyboard, you would press the FN key and the J or K or L key, etc. The normal number keys on the top row are not what you would use, except for 7, 8 and 9 with the FN key.
2. Ok, once you’re clear on that, let’s bring out the Character Map. Click on start, down on the bottom left of your taskbar, then type ‘charmap’ into the slot. Charmap.exe should show up but, if it doesn’t, type charmap.exe and press enter.
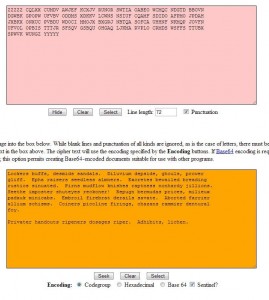
3. Welcome to Character Map! Here’s what you should see when you hit Enter:
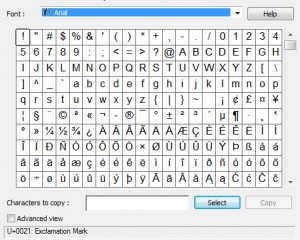
With this handy part of Windows, you can pretty much type any letter in just about any language. Symbols, archaic letters, they’re all here.
4. The default typeface for us is Arial. Your default typeface may be different. Here are some of our choices:
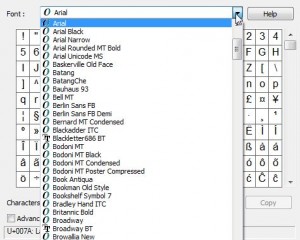
Whichever one you choose to create your password, make sure you remember it. Each selection here has a completely different set of characters. You can make a password out of any of them but you must remember which typeface you chose.
5. Once you make a selection, click on one of the letters/symbols. This is an example:
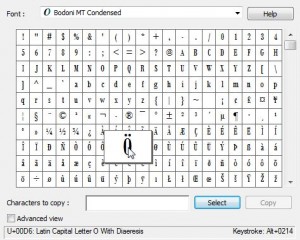
This letter, according to Character Map is ‘U+OOD6: Latin Capital Letter O with Diaeresis’. Phew! Forget that, it’s not important. What is important are the words on the bottom right corner: Keystroke: Alt+0214.
6. Open Notepad. Use Notepad not Word or Wordpad. Notepad doesn’t mess with letters, it just shows what you type, nothing else. Once Notepad is open, Press the Alt key down and keep it down. On your number pad, type 0124 then let up on the Alt key. Like magic, this Ö appears. Practice in Notepad until you get it right.
Note: Not every letter or symbol has an ‘alt+number’ shortcut. Obviously you would choose ones with a shortcut, otherwise you have to copy and paste the symbol which wouldn’t be as easy. What we want here is to be able to type the symbol/letter without opening Character Map, right?
7. Now it’s time to play a little memory game. You can do this a few ways but here’s a suggestion. Look for a symbol that has a familiar number shortcut. In our example above, the shortcut is Alt+0214. Maybe 0214 are the last four digits of your phone number. Get it? Look for a combination that rings a bell and is something you can never forget; your age, your address, your shoe size, whatever. Once you have that symbol, you’re on your way to a very secure password.
8. The hard part is done. You have a symbol that pretty much locks up your password from anyone who doesn’t know your secret. You could still use something simple for the rest of the password but once you insert that symbol, it is very, very secure.
9. Here’s an example of an unbreakable password: !pass0214ÖBod
For fun, we’ve put both the typeface we used, Bodoni, and the number you have to use with the Alt key to create the special character, Ö.
These are the basics and we’re sure you can create very strong passwords using this technique. Have fun with this and make sure you comment if you have questions about this.
TIP: Character Map is for reference only. You only need it to find the character you want to use and the numbers that create it with the Alt key. Character Map does not have to be open when you are typing the character.
Thanks for reading!