In our last post, we described how to encrypt an email using JavaScrypt, a simple but effective way to hide your personal information from prying eyes. That post is here: Encrypt Your Emails For Free. Today’s post assumes that you’ve read the linked one so, if you haven’t read it yet, head over and check it out. We’ll wait…
Back? OK, here we go. The message that we used yesterday was very simple but the encoded message was obviously encrypted. What if we still wanted to encrypt a message but didn’t want it to look as if it was in code? It’s pretty clear that an encrypted message would raise suspicions about its content, even if that content was completely innocent. Here’s how to solve that problem.
Steganography is the term for this process, hiding something in plain sight. There are several ways to do it but, for now, let’s stick with what we learned yesterday. To accomplish this task, you must have two browser windows open. First, open up the link from yesterday’s post. Here it is: JavaScrypt Encryption.
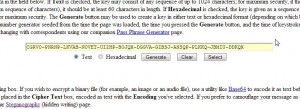
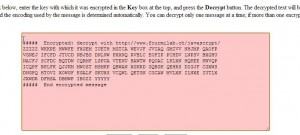
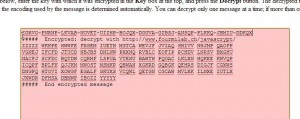
When the page opens, run through the same process as we described previously, generate a code, write a simple message and then encrypt it. You’ll end up with something that looks like this:
It’s painfully obvious that this is an encrypted message. Let’s make it look like bad poetry. Open this page: Stego! Text Steganography. Both pages are by the same person, more on him later, so they look very similar. What we’re going to do here is simply copying and pasting from one browser window to the other. Our aim is to hide the encrypted message in text that looks vaguely normal, in other words ‘words’. Let’s get going:
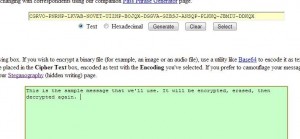
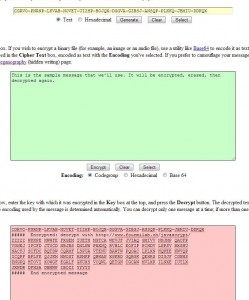
1. We will use the encrypted message in the photo above. Highlight it then right click and choose Copy. Go to the Stego page (link just above this), click in the pink box, right click and choose Paste. Under the pink box is the word Hide. Click it.
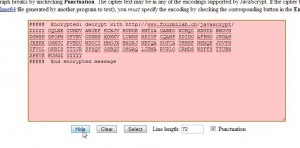
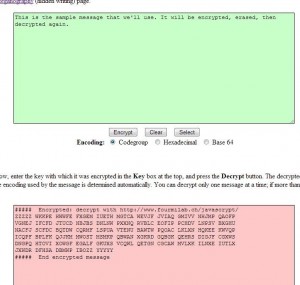
2. Once you click the Hide button, a new message appears in the orange box at the bottom.
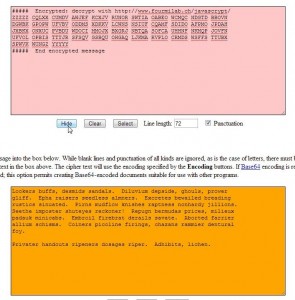
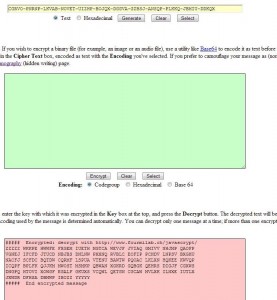
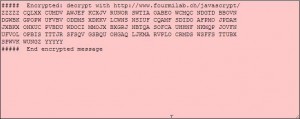
3. What we have now is an encrypted message that has been transformed into something that looks a bit less intimidating and a whole lot less suspicious. What do we do now? We can’t decrypt this gibberish, not directly anyway. We have to ‘unhide’ it. Normally you would have to copy the words from an email then paste them into the orange box. For now, just erase the encrypted message in the pink window and leave the words in the bottom window. Like this:
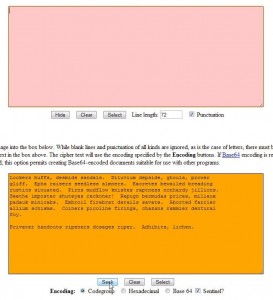
4. Click Seek and the original encrypted message will appear in the top box again.
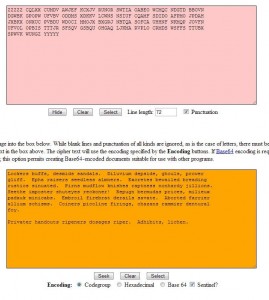
This two page, multi-step process takes an email, or any text document for that matter, encrypts it, then changes the encrypted message into something that resembles normal English. If this text happened to be buried in a much longer document, there’s a good chance that it wouldn’t be noticed. While this whole thing takes a bit of extra time, we think you’re more likely to slip beneath the radar, if you know what we mean.
TIP: In order to use this system, all of the settings have to be the same for the encryption and the decryption as well as for the ‘hiding’ and ‘seeking’. Each page of the site gives you ample information to change the settings to your own specifications but be sure to make a record of those settings if you want to have a problem-free experience.
The site that we’ve linked to here belong to John Walker, co-creator of the Autodesk company and its software (AutoCad). Both pages that we’ve mentioned can be downloaded and run on your computer, no Internet connection is necessary. In other words, you could perform all of your encryption/decryption tasks ‘offline’.
Should you encrypt your emails? That’s up to you. We don’t but we sleep a bit better knowing that, if the need arises, we could. If you think the process described here is new, it’s not. The two pages we’ve mentioned were created in 2005. We are not naive enough to think that this simple encryption process is invincible to decryption by a third party and neither should you. What we have described here will keep your private information out of the hands of people who shouldn’t be snooping in your stuff anyway. Besides, it’s fun to experiment with this and it makes very interesting chatter at the dinner table, right?
Thanks for reading! Like us on Facebook and you’ll be able to keep up with our latest news and posts: Computer Made Simple on Facebook.