If you’re confused about what virus, malware, adware, and Trojans, etc. are, here are some definitions for you:

1. Virus
This is an all -encompassing term but, fortunately, it’s a type of malware that we don’t see to often these days. A virus in a computer performs pretty much the same as it does in a human; it takes over completely, preventing other systems from working. A bad virus in either host can sometimes destroy that host completely. Many viruses were written to simply show the awesome skill of the person who wrote the script. Read that with heavy sarcasm. Some script kiddies , as they are sometimes called, don’t even write their own stuff. They copy scripts from more knowledgeable coders and claim them as their own, often signing their names somewhere in the virus code. These days, this type of individual would rather leave their work unseen and unnoticed by the users that they try to infect, in order to extract as much information as possible from them. A virus seeks to attach itself to as many files as it can on the host computer. This is the activity that your AV software should pick up. It’s the speed of the replication that makes them so very dangerous.
2. Malware
Anything that does damage, extracts private information or uses someone’s computer for purposes unknown to that user could be termed malware. There are many different kinds but, basically, things that do bad stuff to computers are designated as malware.
3. Adware
Adware is not nearly as bad as malware but it is aggravating and frustrating all the same. Most adware is installed with those seemingly helpful toolbars which many companies install with their software. Adware wants you to use a certain page for your homepage, a specific search engine, etc. Adware pretends to help you but, in reality, it only helps the company that installed it on your computer. One of the main problems with adware is that it frequently is missed by your anti-virus software. It’s not really harming your computer and it doesn’t act like malware so your AV program will likely not even notice that it’s running or pick it up on a scan. There are specific programs that seek out and destroy adware and we’ll get into these in a future post.
4. Trojan
These are things that pretend to be other things, just as the original Trojan Horse pretended to be a gift way back in history. The computer user expects a file to be a certain thing, let’s say a Word document or PDF, but that file is actually the installer for a piece of malware. The unwitting computer user won’t know what’s going on behind the scenes when they click on the infected file. While everything may seem normal and the software may do exactly what the user expects it to do, it has also infected the computer with any one of dozens of kinds of malware. It’s not only hackers that do this. Governments use Trojans to manipulate computers and machinery in countries that may be a threat to them. If you’ve ever heard the term ‘backdoor’ in discussions of malware, this is what a Trojan seeks to install on the host computer. Once the backdoor is up and running, the infected computer can be manipulated without its owner knowing about it.
5. Worms
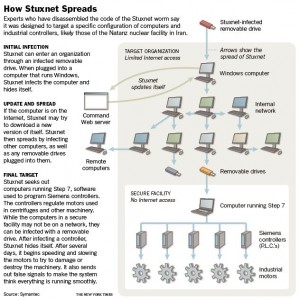
Probably the most famous computer worm is known as the ‘Stuxnet’ worm, designed expressly to infect Iran’s nuclear engineering projects. A worm is a virus but isn’t quite as bent on destruction as a simple virus is. Worms can do many things but their aim is to sit unnoticed, all the while feeding information out to the installer and, in some cases, preventing devices from performing as they should. If one country wants to eliminate a perceived threat, let’s say from a missile installation, it is possible to have those missiles misfire or go off-course through the use of a computer worm. If you’re familiar with the TV series Battlestar Gallactica from about ten years ago, you’ll remember that the Gallactica, which was not networked, was the only spaceship which was not infected with the virus that destroyed the defence capabilities of every other networked military ship. Worms work their way from computer to computer though networks, often through updates. Some worms are designed specifically to target certain types of mechanical systems.
Those are the basics. In our next few posts, we’ll show you how to immunize you and your family from these threats. While dangers do not lurk in every corner of the Internet, there are enough of them out there to make knowing this stuff very important. Tell your friends!
Thanks for reading!
