Just this morning we read that 100% of attacks on computers are criminal in nature. What does that mean? Simply that hackers aren’t out just to have fun, they are actively trying to steal your personal information. It’s not only personal computers that are under attack. Read this story about how a major Canadian bank was scammed out of $87,000.00: Bank of Montreal Gets Scammed Once you read the story, you’ll see how all of this started. The customer’s email account, which had been hacked, was used to initiate the process.
We’ve written posts about how you can protect your email account(s). Here’s a link that shows some of them: Email Password Protection Make sure you read as much as you can about using a strong password as well as how to enable two-step authentication. For that matter, make sure you use multi-level authentication for virtually everything you do online. Most email providers as well as banks, social networks and financial institutions already require this. Make sure you take advantage of it.
Enough preamble, let’s get to a new type of scam that you might fall prey to. This involves Google Maps. Bear with us while we explain how it works:
1. If you run a business, you can put your location and business information right there on the Google map of your city, complete with your street address, your logo and your phone number. This is where the danger is, that phone number.
2. Hackers have found a way to install fake telephone numbers in Google Maps. Let’s say you’re looking for a bank branch in another city. It’s easy to check a bank’s name, just type it in and you’ll immediately see little flags all over the map. This works for anything, restaurants, hardware stores, police stations, etc. Here’s an example of the information you might see:
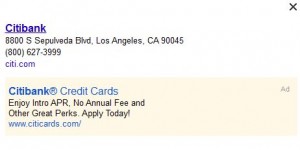
3. Before you call the Citibank number, it might be a good idea to check the number somewhere else, let’s say on Citibank’s real website. Use the map for the location but NOT for anything else. This doesn’t apply only to banks. Here’s a link to the story explains the exploit and how several people thought they were calling the FBI but were really calling a hacker, this time an honest one:
FBI and Secret Service Calls Intercepted by Google Maps Exploit
These are a few things to watch out for when you’re online. In our next post, we’ll get into a bit more depth on these scams and how you can protect yourself from them. Stay tuned. In the meantime, ask questions or comment below or on our Facebook page. Here is the link to it:Computers Made Simple on Facebook.
Thanks for reading!
________________________________________________
Here’s a link that might help us if you are interested in hosting your own blog with Fatcow Hosting. We’ve signed up to become an affiliate and we make a bit of money if you sign up for hosting via this link: FatCow Hosting Thanks!