This is the last post on encryption for a while. Today we’re going to show you how to lock up your DropBox storage folder, both online and on your computer.
(In case you don’t know about DropBox, you should really check it out. We’ve written several posts on this free and very cool service so search our site or head over here and sign up for your free 2 gigs of space. Here’s how DropBox works: Post 1 Post 2 We’ve also written about how Dropbox can ‘save your bacon’. It really can! Here’s a link to that post: How DropBox can Save Your Bacon)
In spite of what DropBox says about its encryption and the safety of your files in its Cloud, don’t believe it. At the drop of a hat, DropBox will open up your private files to anyone who asks. Anyone with a badge that is. What’s the problem with that? We’re all for law and order but we don’t think anyone should be able to go through your personal files without you knowing about it. Even if no one in authority has an interest in your stuff, the employees of DropBox can and do sift through your files on a regular basis. Microsoft does this too, this kind of thing is not limited to DropBox. Let’s just say that everyone does the same thing.
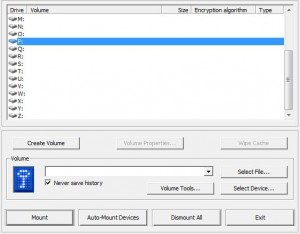
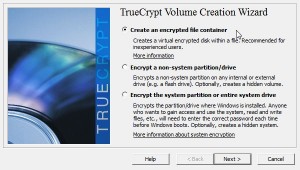
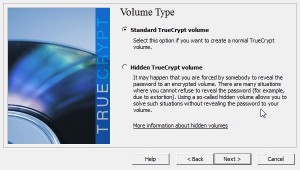
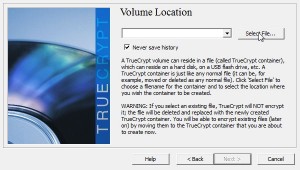
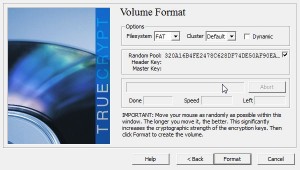
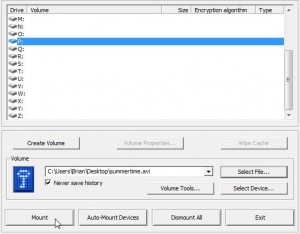
Once you’re clear on that, here’s how to keep your information private. You made an encrypted container right? We showed you how to do that in our last post. Here’s the link in case you missed it: Encrypting Your Stuff – Create a TrueCrypt container for DropBox. You should make more than one container. Instead of putting everything in one locked volume, consider making several. Let’s say you make one for passwords, one for personal photos, one for videos, one for financial information, etc. That way, you don’t have to upload a massive folder every time you do some work on the things in that folder. We’ll explain that next.
DropBox keeps your stuff online AND on your computer(s). The beauty of DropBox is that you can access your material from any computer anywhere in the world. Sometimes you will access your online folder using a browser. Other times, when you’re on one of your own computers, you will access your stuff in the folder that is on your hard drive. DropBox automatically syncs that folder every time you go online. If you access your folder in a browser, DropBox syncs any changes that you made with the folder that’s on all or any of your computers the next time you go online. You don’t have to worry about any of this, it’s all done automatically.
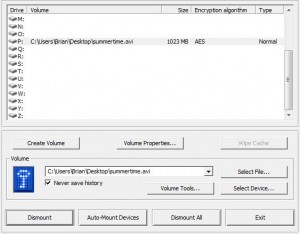
All you have to do is make sure that your encrypted containers/volumes/folders are in the DropBox folder on your computer. As soon as you put the encrypted volumes there, DropBox syncs everything automatically, any time there are changes. It really is that simple.
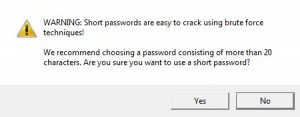
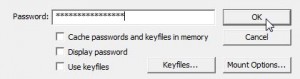
Knowing all of this, you’ll probably agree that this is the best way to hide your personal information online and on your own computer(s). If your house is broken into or if you lose your laptop, anyone can access that information if it’s not encrypted. Don’t wait for that to happen, do it now! Don’t keep the TrueCrypt password on your computers, that’s kind of obvious but we thought we’d mention it.

TIP: Use several small containers instead of one large one. That makes syncing much faster. As mentioned above, encrypt a few 10 MB containers and label them accordingly. If you do need a larger container for a video, for example, you probably won’t change it too much so syncing time won’t be an issue.
That’s it for now. If you have questions, comments, suggestions, please let us know.
Thanks for reading! Why not Like us on Facebook? Here’s the link: Computers Made Simple on Facebook